Securing your assets
Getting to know the tools
1. Enterprise access model
The Enterprise Access Model is a way to secure access to your company's data and systems. Here's the breakdown:
- Think of it as a layered security plan. It splits your IT infrastructure into different sections based on how sensitive the information is.
- Most secure areas get the tightest controls. Only authorized people with minimal access can enter these areas. Imagine a vault for critical systems like domain controllers.
- Other areas are less restricted, but access is still controlled. Think of this as access to applications and data depending on an employee's role. A marketing team might not need access to engineering data.
- Security is always on. We double-check everyone's identity and only grant the minimum access needed to do their job.
- It works for all your IT environments. Whether it's on-premises servers, cloud storage, or remote access, the model ensures consistent security. This approach helps prevent unauthorized access and keeps your company data safe from potential threats.
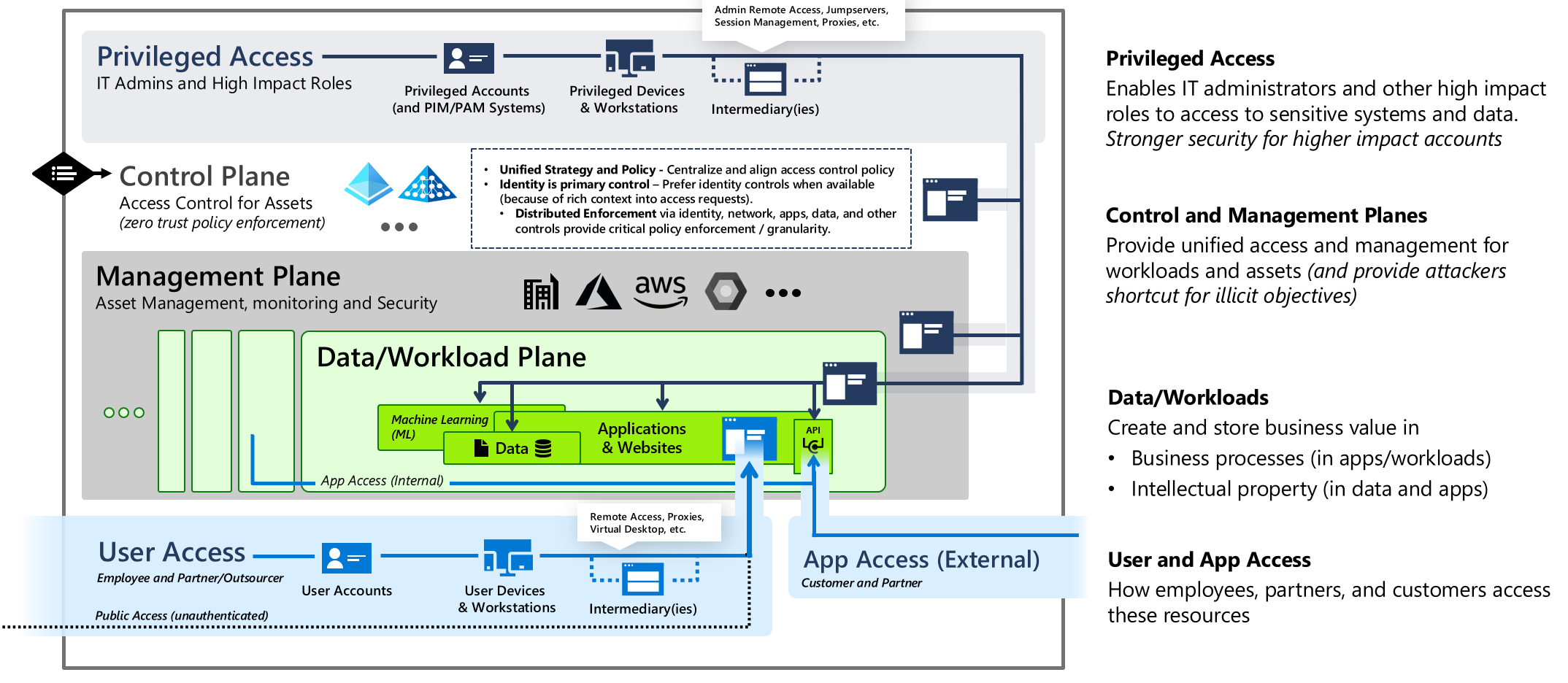
- Data/Workload Plane: This layer encompasses all the applications, databases, and files that an organization relies on. It’s where the real work happens the digital machinery behind the scenes.
- Management Plane: Think of this as the control center. IT professionals manage and oversee systems here. They ensure everything runs smoothly, like air traffic controllers guiding planes safely through the skies.
- Control Plane: Here’s where security takes center stage. The Control Plane verifies identities before granting access. Whether it’s a user logging in or an application requesting data, they need proper credentials.
- User Plane: This is the interface where users interact directly with applications and data. It’s the bridge between people and technology.
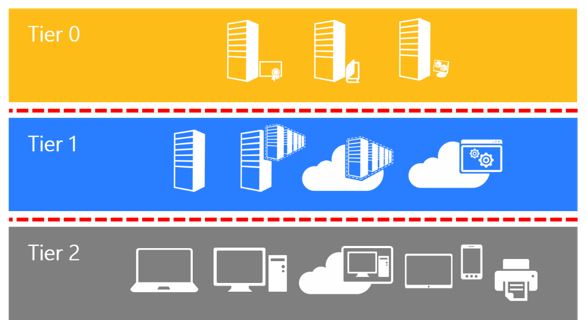
The legacy Enterprise Access Model, also known as the Tier Model, was an earlier approach from Microsoft for securing access within a company's IT system.
- Imagine three levels of access. Each level had stricter controls than the one below.
- (Tier 0) was the most secure. Only highly privileged users, like IT security admins, could access this level. This is where critical systems like domain controllers lived.
- (Tier 1) housed important resources. Think of this as a server room with business applications and sensitive data. Authorized IT personnel could access this area for maintenance or management tasks.
- (Tier 2) was the least restricted. This is where regular employees accessed their computers and everyday applications. Security wasn't as tight here, but access wasn't wide open either.
The Tier Model was mainly designed for on-premises servers and didn't consider complexities, like cloud.
2. Priviliged Access Workstation (PAW)
Absolutely, as an IT security engineer, I can tell you all about a Privileged Access Workstation (PAW).
A PAW is a special kind of computer designed for high-security tasks. It's essentially a locked-down workstation built for users with administrative privileges, like system administrators. These users manage critical systems and data, so it's essential to keep their access secure.
Here's what makes a PAW special:
- Isolation: PAWs are isolated from the internet and other potential threats. This means no web browsing, email, or other risky activities on the PAW itself. It minimizes the attack surface, making it harder for attackers to exploit vulnerabilities.
- Security Controls: PAWs have strict security controls. Local administrator access and even some productivity tools are restricted. The focus is on providing only what's absolutely needed for those high-risk tasks.
- Dedicated Use: PAWs are dedicated workstations for privileged users. They shouldn't be used for everyday tasks like checking email or browsing the web. Separate workstations should be used for those activities.
By isolating privileged accounts and activities, PAWs make it much more difficult for attackers to gain a foothold in your systems, even if they compromise a privileged account.
3. Jump Host
A Jump Host is a special-purpose computer on a network specifically designed and configured to provide access to a private network from an external network, such as the internet.
The idea behind a Jump Host is to create a single point of entry into a network for security purposes. This host is typically highly secured and monitored.
This setup provides several benefits:
- Security: By limiting access to your internal network only through the Jump Host, you reduce the surface area for attacks.
- Monitoring: It's easier to monitor and audit traffic when it's all going through a single point.
- Management: User access can be managed more effectively. For example, changes to access policies need only be implemented on the Jump Host.
In essence, a Jump Host acts as a bridge between two networks, providing a controlled means of access between them. It's an important concept in network security, particularly in cloud computing environments.
Bringing the tools together into one concept
Firstly why should you use these or related tactics to secure your Infrastructure? This is the easy part. Many of the above strategies are part of the one or other Zero Trust framework. But beyond Zero Trust, securing your most precious digital assets is one of the most important things you need to do as an IT Leader. With bringing specifically these tools together, there is a way to protect one, two or however many tiers of differend assets you have, without having to invest in a full Zero Trust framework.
But how? I here you ask.
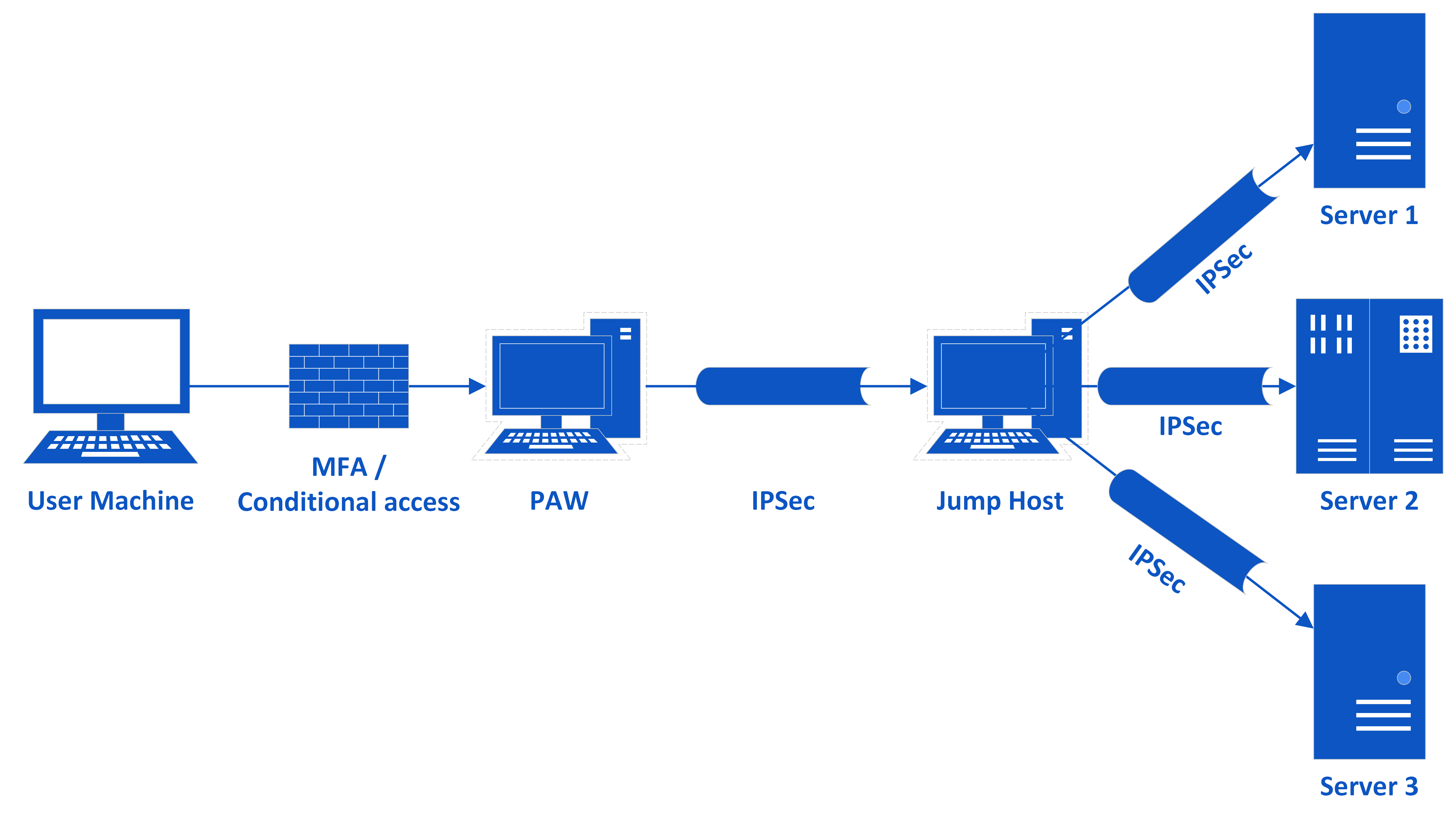
- Like seen in the diagram we can use an adapted PAW, as the entry point. This should be a cloud VM or at least a normal VM, but it can of course be a physical machine.
- Adapted in the sense, that it is reachable from the outside, but it needs to be locked down, so nothing can be done with it, infiltrated or exfiltrated through it.
- In addition the access is secured through MFA, conditional access and varoius other security meassures.
- This PAW connects then via IPSec to a Jump Server. This Jump Server can only be reached from this PAW. From nowhere else are connections excepted.
- Not only RDP, but all connections.
- This Jump Host can then connect to the assets (Server, Firewalls, etc.) you want to protect.
- Or the Jump Host can hold the tools to control these assets.
- The connection to the assets are in turn via an IPSec tunnel and they will only accept connections from this Jump Host or a Group of Jump Hosts (depending on the volume of connections).
- In addition to the traffic from the Jump Hosts the assets will accept traffic regarding there specific use (Application Traffic for example).
- Connections will be be dropped after a certain amount of inactivity and disconnected sessions will be dropped immediatly.
- The PAW will be wiped after use immediately or directly redeployed.
With this adaptation and combination of the previously mentioned concepts, you can relativly low cost purpose build secure connections to especially importand assets and even use remote access. It is not ideal and doesn`t employ all zero trust elements, but it is a good start to make important assets like domain controllers or business relevant databasses much more secure, protecting them from vertical attack movement and RAM dumping technics. In addition the attack surface is enormously reduced and there is a much lower chance of a breach and easier monitoring.