Passwordless authentication in a hybrid environment
👋 Introduction
In an era of accelerating digital transformation, traditional password-based authentication is increasingly becoming a pain point for both security and user experience. As organizations transition there environments to the cloud, but still need to incorporate on-premises resources, hybrid environments are becoming the norm.
By blending on-premises infrastructure with cloud-based solutions, the need for a more secure and seamless authentication method is paramount. Passwordless authentication emerges as a game-changer, offering a phishing resistent solution that enhances not only security but also simplifying authentication for users.
This article delves into setting up passwordless authentication in hybrid environments.
✅ Prerequisites
- Your Windows Server domain controllers must run Windows Server 2016 or later
- Devices must be running Windows 10 version 2004 or later.
- Devices must be joined or hybrid joined to Microsoft Entra ID
- Users must have the following Microsoft Entra attributes populated through Microsoft Entra Connect or cloud sync:
- onPremisesSamAccountName (accountName in Microsoft Entra Connect)
- onPremisesDomainName (domainFQDN in Microsoft Entra Connect)
- onPremisesSecurityIdentifier (objectSID in Microsoft Entra Connect)
- Devices need to reach the following endpoints to reach Entra ID:
- *.microsoftonline.com
- *.microsoftonline-p.com
- *.msauth.net
- *.msauthimages.net
- *.msecnd.net
- *.msftauth.net
- *.msftauthimages.net
- *.phonefactor.net
- enterpriseregistration.windows.net
- management.azure.com
- policykeyservice.dc.ad.msft.net
- secure.aadcdn.microsoftonline-p.com
⛔ Unsupported scenarios
The following scenarios aren't supported:
- Active Directory joined (AD DS) devices (on-premises only devices).
- Remote Desktop Protocol (RDP), virtual desktop infrastructure (VDI), and Citrix scenarios by using a security key.
- S/MIME by using a security key.
- 'Run as' by using a security key.
- Log in to a server by using a security key.
🧑🔧 How it works
To create a cloud Kerberos trust, you need to use a PowerShell script in Active Directory (AD). This process involves setting up Entra ID as a read-only domain controller (RODC) in AD. Once this is done, Entra ID will have a Ticket Granting Ticket (TGT) for Kerberos authentication. This means that when someone logs in using Windows Hello for Business, they can authenticate against the cloud and receive a Kerberos ticket, allowing AD to authenticate them as well.
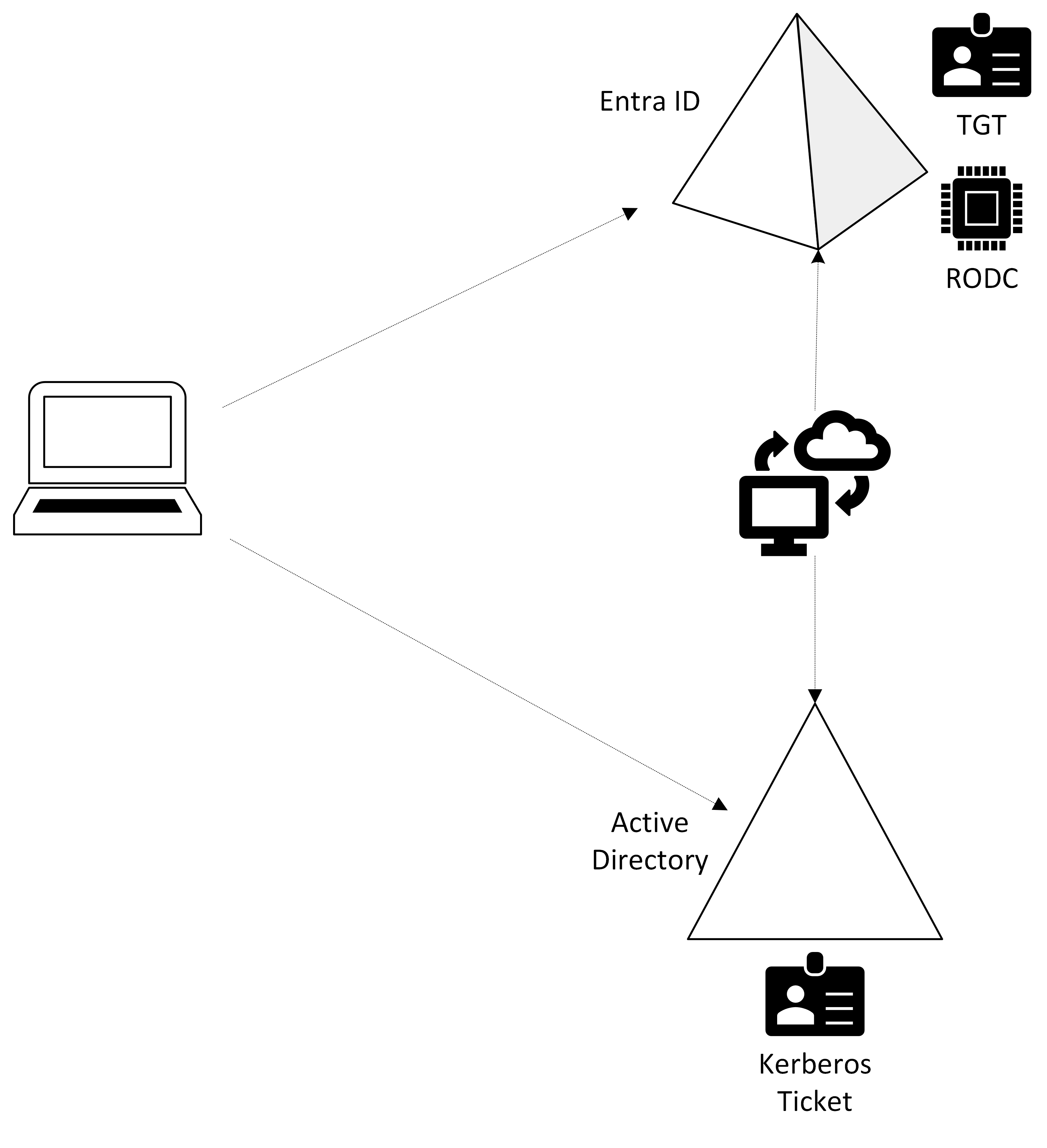
Microsoft Entra join authentication to Active Directory using cloud Kerberos trust
INFO
In this example the devices are Microsoft Entra joined.
- Phase 1: Authentication to Active Directory from a Microsoft Entra joined device begins with the user first attempts to use a resource that needs Kerberos authentication.
The Kerberos security support provider, hosted in LSASS (Local Security Authority Subsystem Service), uses metadata from the Windows Hello for Business key to get a hint of the user's domain. Using the hint, the provider uses the DClocator service to locate a domain controller. - Phase 2: After locating a domain controller, the Kerberos provider sends a partial TGT (Ticket Granting Ticket) that it received from Microsoft Entra ID from a previous Microsoft Entra authentication to the domain controller. The partial TGT contains only the user SID, and it's signed by Microsoft Entra Kerberos.
The domain controller verifies that the partial TGT is valid. On success, the KDC (Kerberos Key Distribution Center) returns a TGT to the client.
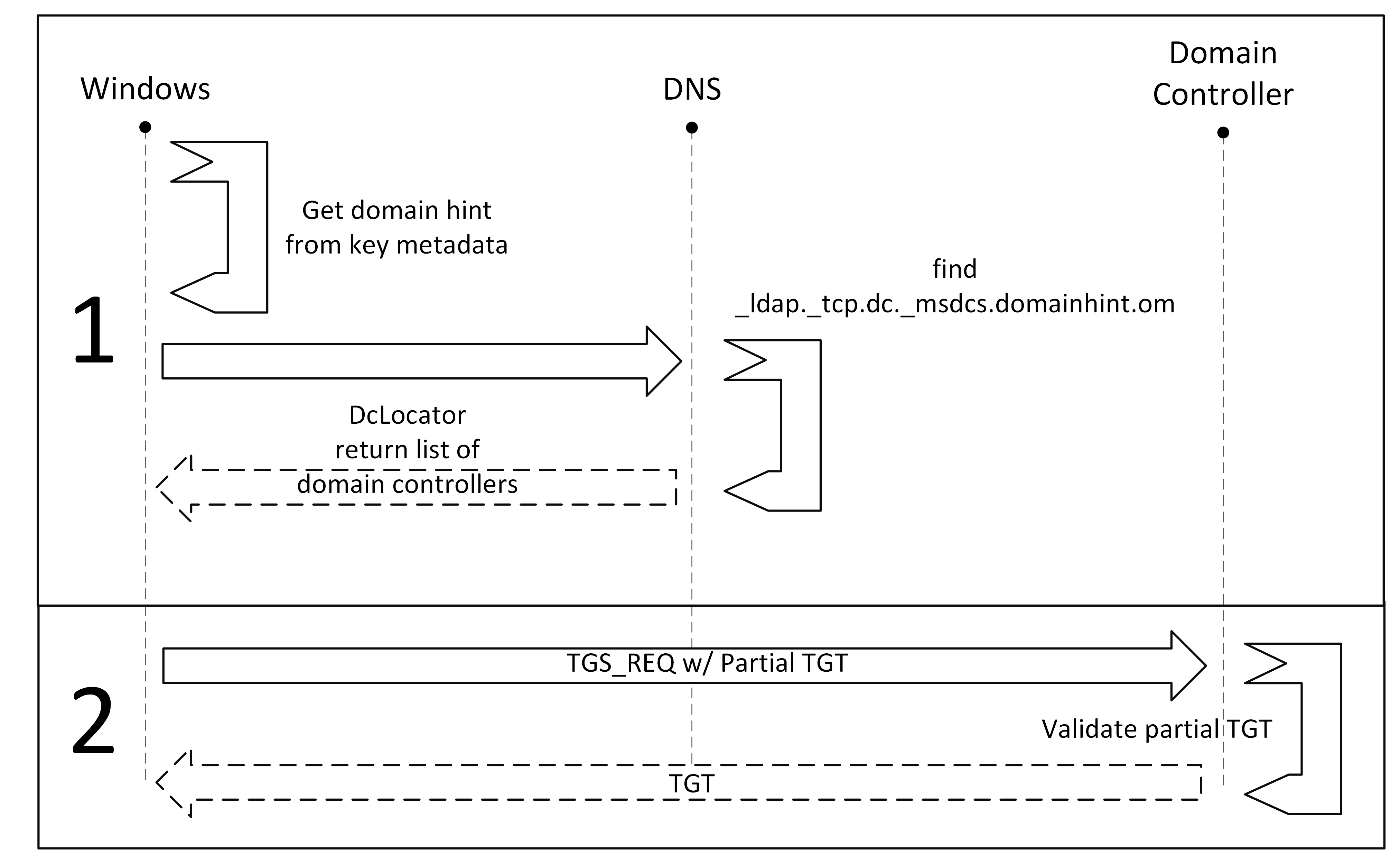
How it looks from the enduser side to use SSO to sign in to on-premises resources
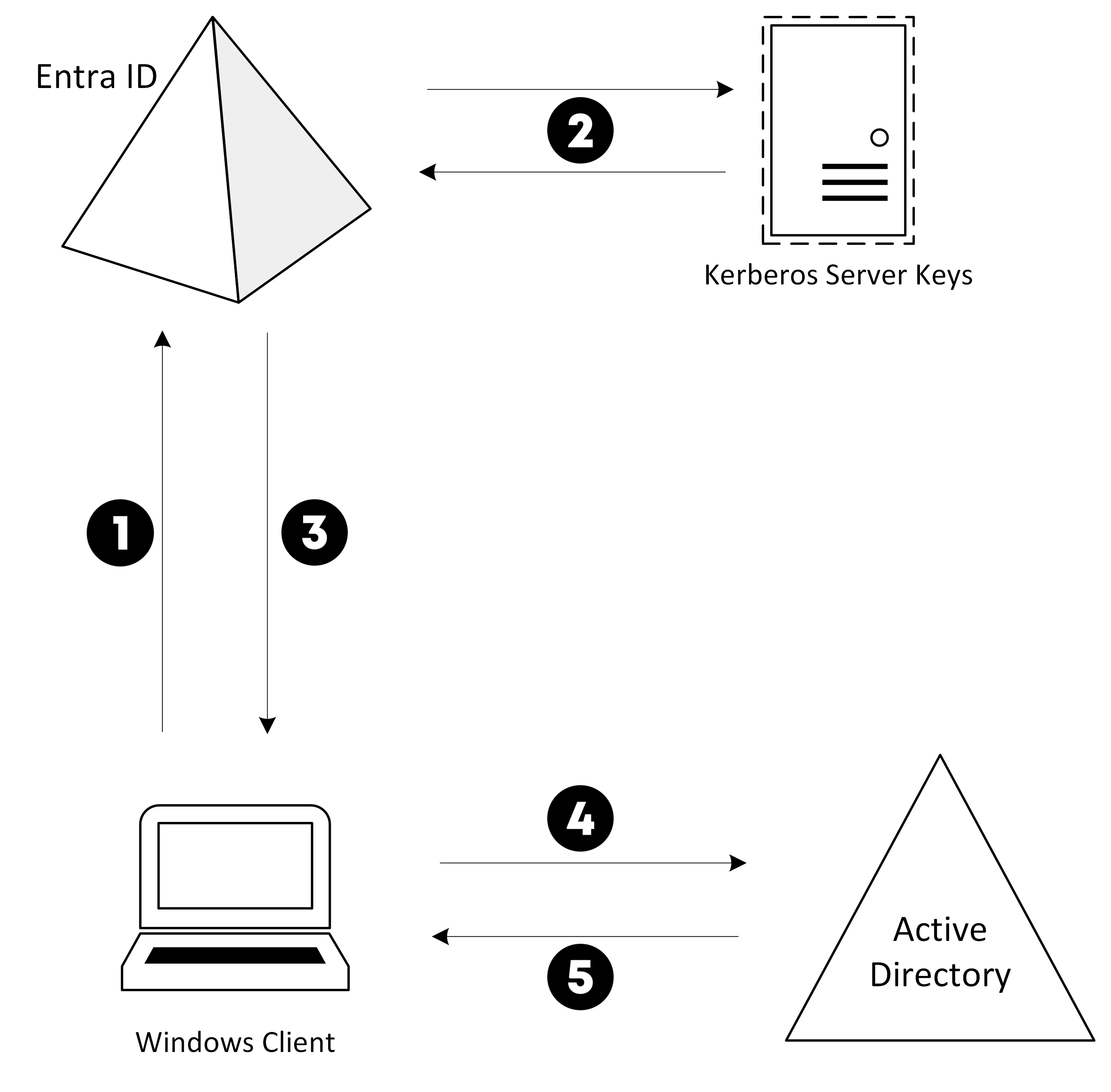
- A user signs in to a Windows 10 device with passwordless authentication to Microsoft Entra ID.
- Microsoft Entra ID checks the directory for a Kerberos Server key that matches the user's on-premises Active Directory domain.
Microsoft Entra ID generates a Kerberos TGT for the user's on-premises Active Directory domain. - The TGT is returned to the client along with the user's Microsoft Entra Primary Refresh Token (PRT).
- The client machine contacts an on-premises Active Directory Domain Controller and trades the partial TGT for a fully formed TGT.
- The client machine now has a Microsoft Entra PRT and a full Active Directory TGT and can access both cloud and on-premises resources.
▶️ Execution
Configure the domain controllers
First we need a device from which you can access the domain controller.
From there we need to make sure that the Network security Encryption Type 'AES256_HMAC_SHA1' is enabled on your domain controllers.
If you want to know more about the different encryption types, you can find out more here.Make a new Group Policy Object (GPO) and link it to your domain controllers.
- Policy:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Network security - Value:
Configure encryption types allowed for Kerberos = AES256_HMAC_SHA1
- Policy:
Next we need to set up the Microsoft Entra Kerberos object
# Ensure TLS 1.2 for PowerShell gallery access.
[Net.ServicePointManager]::SecurityProtocol = [Net.ServicePointManager]::SecurityProtocol -bor [Net.SecurityProtocolType]::Tls12
# Install the AzureADHybridAuthenticationManagement PowerShell module.
Install-Module -Name AzureADHybridAuthenticationManagement -AllowClobber- Now we need to promt for all needed credentials using modern authentication and create the Entra ID Kerberos Server Object in the Active Directory domain.
# Specify the on-premises Active Directory domain. A new Microsoft Entra ID
# Kerberos Server object will be created in this Active Directory domain.
$domain = $env:USERDNSDOMAIN
# Enter a UPN of a Hybrid Identity Administrator
$userPrincipalName = "administrator@yourdoamin.com"
# Enter a Domain Administrator username and password.
$domainCred = Get-Credential
# Create the new Microsoft Entra ID Kerberos Server object in Active Directory
# and then publish it to Azure Active Directory.
# Open an interactive sign-in prompt with given username to access the Microsoft Entra ID.
Set-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential $domainCred- Next we can view and verify the Microsoft Entra ID Kerberos Server Object.
# When prompted to provide domain credentials use the userprincipalname format for the username instead of domain\username
Get-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential (get-credential)
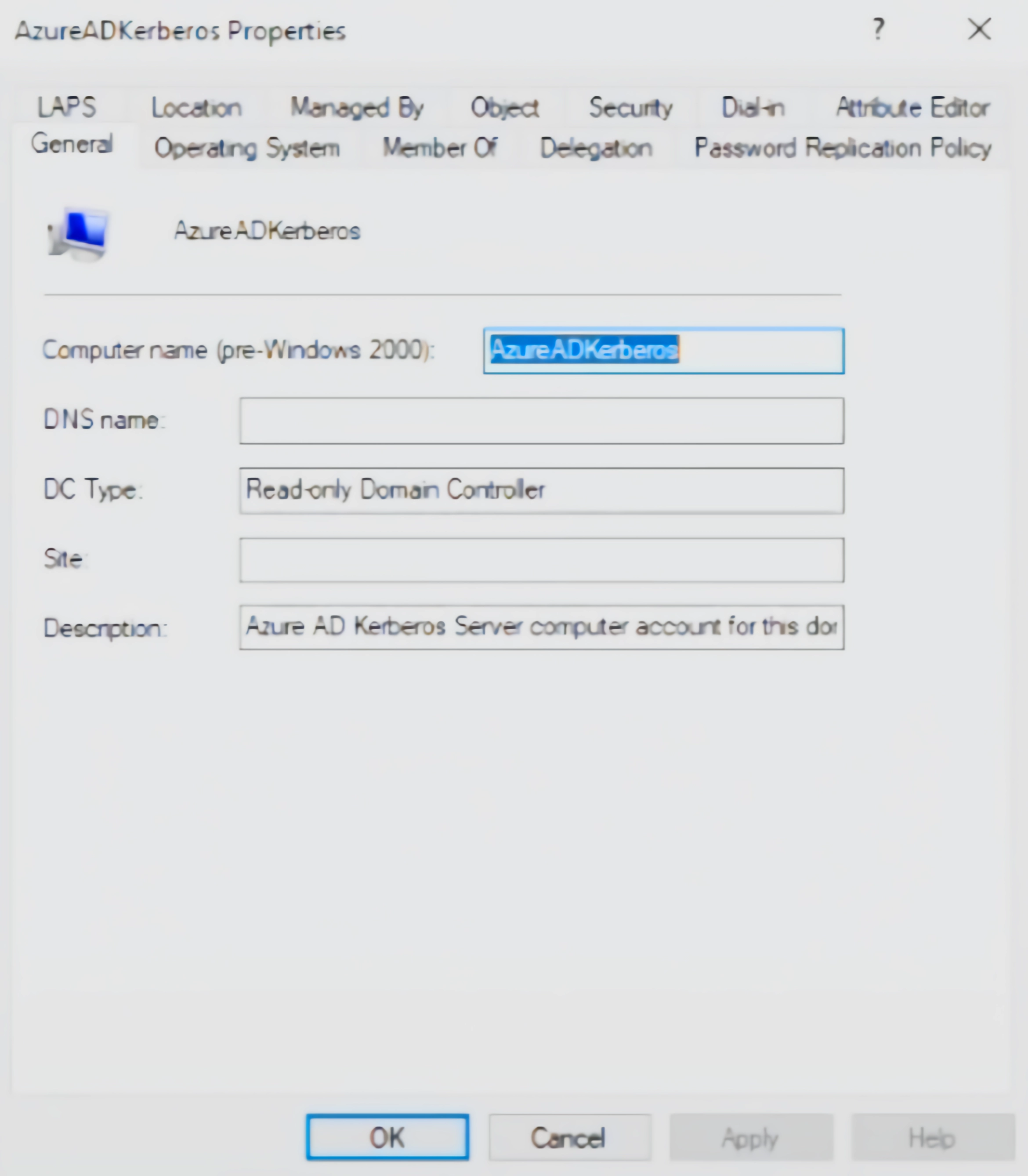
Details
Rotating the Microsoft Entra Kerberos server key
The Microsoft Entra Kerberos server encryption 'krbtgt' keys should be rotated on a regular basis. It is recommended that you follow the same schedule you use to rotate all other Active Directory DC 'krbtgt' keys.
Set-AzureADKerberosServer -Domain $domain -CloudCredential $cloudCred -DomainCredential $domainCred -RotateServerKeyConfigure passwordless authentication (Windows Hello for Business)
Using Microsoft Intune
- Open the Intune admin center and select Devices -> Configuration -> Create.
- Platform: Windows 10 and later
- Configuration profile type: Settings catalog
- Name and describe the policy and click 'Next'
- Add the following settings:
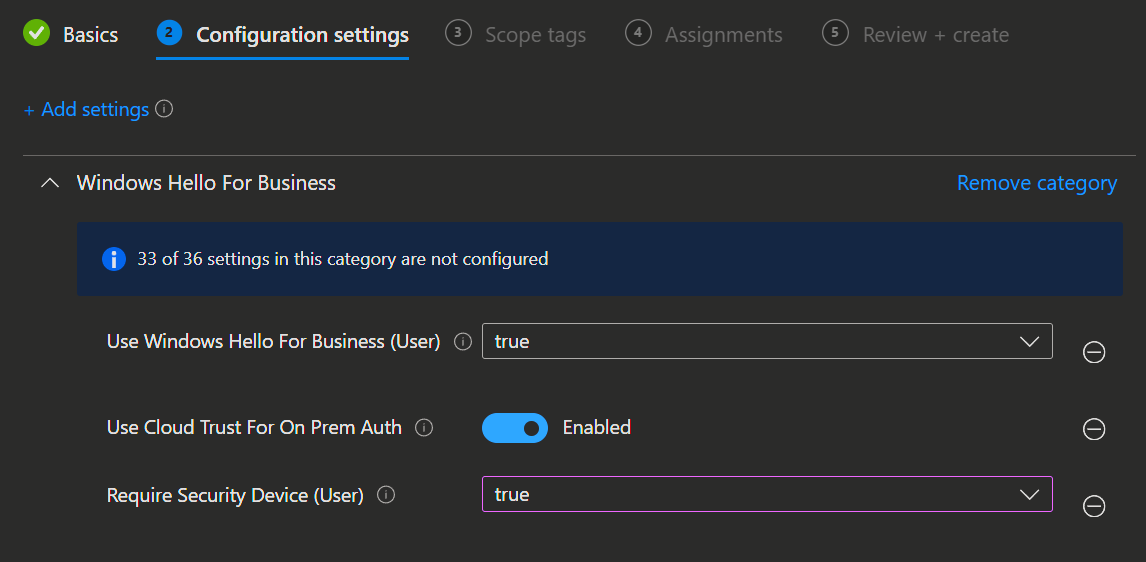
Category Setting name Value Windows Hello for Business Use Windows Hello For Business true Windows Hello for Business Use Cloud Trust For On Prem Auth Enabled Windows Hello for Business Require Security Device true - Click 'Next', 'Next', select your assignd groups (Users or Devices are fine), click 'Next' again and 'Create'.
Using Group Policy
- Open the Goup Policy Management console on your Domain Controller and create a new GPO.
- Add the following settings:
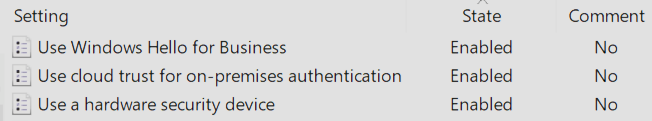
Group policy path Group policy setting Value Computer Configuration\Administrative Templates\Windows Components\Windows Hello for Business Use Windows Hello For Business Enabled Computer Configuration\Administrative Templates\Windows Components\Windows Hello for Business Use cloud Kerberos trust for on-premises authentication Enabled Computer Configuration\Administrative Templates\Windows Components\Windows Hello for Business Use a hardware security device Enabled
- Now link the GPO to your domain or organizational unit.
🧑💻 User Experience
- Now the user can start the process by signing in to Windows.
- There he will be prompted to configure Windows Hello for Business.
- And after that, the user now can access local domain recources with passworddless authentication.