LAPS Updates March 2025
👋 Introduction
LAPS (Local Administrator Password Solution) is a useful tool from Microsoft that automatically manages and backs up the passwords for local admin accounts on Intune or Active Directory-managed devices. It helps improve the security of the notoriously unsafe local admin accounts and, with that, closes another avenue for cyberattacks. It provides admins centrally managed access to these passwords and the capability for automatic event-driven changes.
🔧 Where to configure LAPS
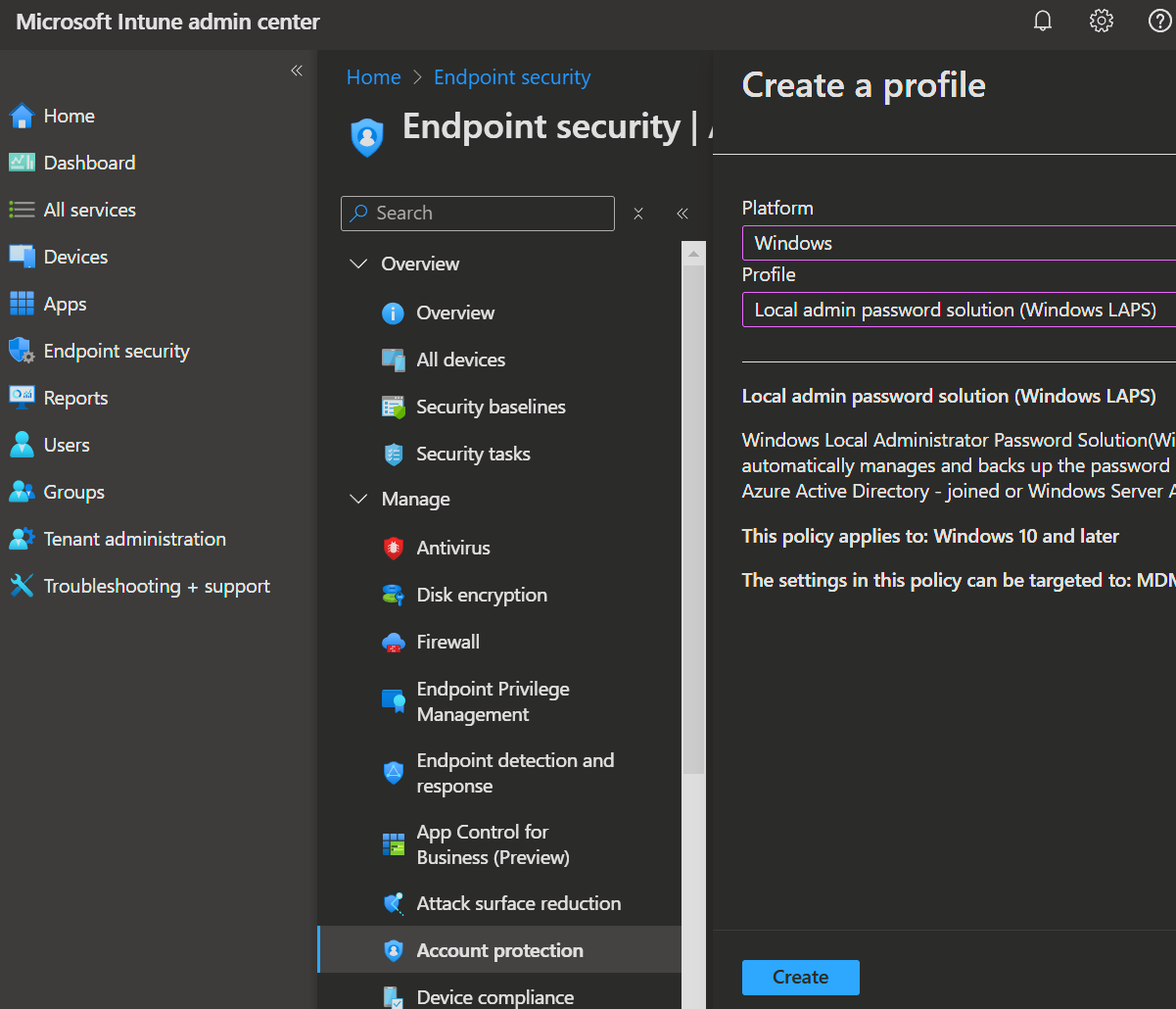
- Open Intune admin center -> Endpoint security -> Account protection
- Now click Create Policy
- Platform: Windows
- Profile: Local admin password solution (Windows LAPS)
- Now enter the 'Name' and 'Description' of your Policy and click 'Next'.
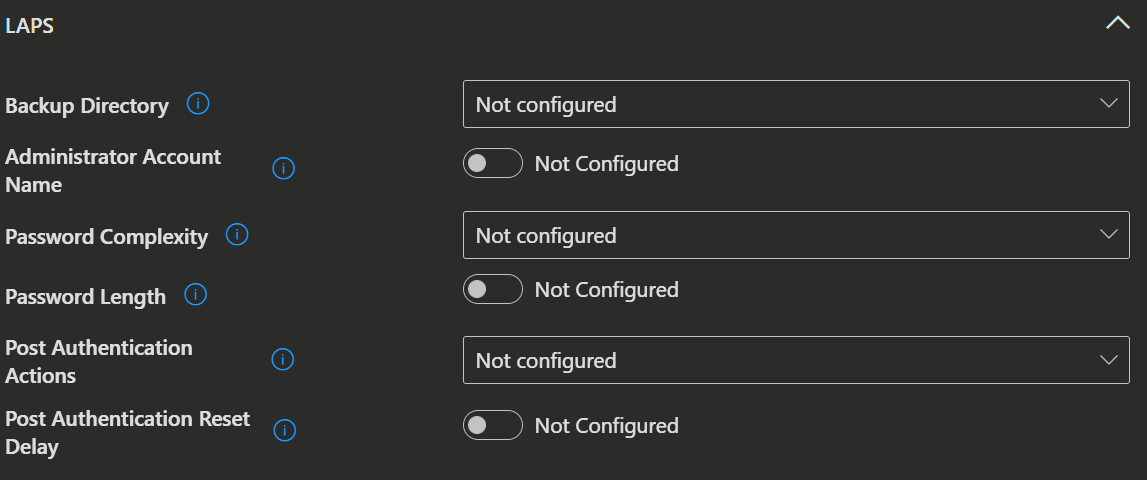
- Here you can configure the already existing settings.
📰 What's new in Microsoft Intune - Week of March 17, 2025 (Service release 2503)
New settings for Windows LAPS policy
Intune policies for Windows Local Administrator Password Solution (LAPS) now include several new settings and updates to two previously available settings. Use of LAPS which is a Windows built-in solution can help you secure the built-in local administrator account that is present on each Windows device. All the settings that you can manage through Intune LAPS policy are described in the Windows LAPS CSP.
The following new settings are available: (Each setting name is a link that opens the CSP documentation for that setting.)
- Automatic Account Management Enable Account
- Automatic Account Management Enabled
- Automatic Account Management Name Or Prefix
- Automatic Account Management Randomize Name
- Automatic Account Management Target
- Passphrase Length
The following settings have new options available:
- Password Complexity – The following are new options available for this setting:
- Passphrase (long words)
- Passphrase (short words)
- Passphrase (short words with unique prefixes)
- Post Authentication Actions - The following option is now available for this setting:
- Reset the password, logoff the managed account, and terminate any remaining processes: upon expiration of the grace period, the managed account password is reset, any interactive logon sessions using the managed account are logged off, and any remaining processes are terminated.
By default, each setting in LAPS policies is set to Not configured, which means the addition of these new settings won't change the behavior of your existing policies. To make use of the new settings and options, you can create new profiles or edit your existing profiles.
What do the new settings do?
IMPORTANT
You need Windows 11 24H2 for these new settings.
Policies/AutomaticAccountManagementEnableAccount
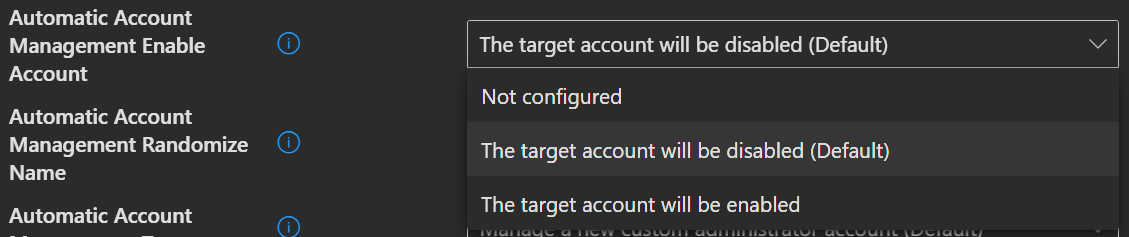
./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementEnableAccountUse this setting to configure whether the automatically managed account is enabled or disabled.
- If not specified, this setting defaults to False.
| Value | Description |
|---|---|
| False (Default) | The target account will be disabled. |
| True | The target account will be enabled. |
Policies/AutomaticAccountManagementEnabled
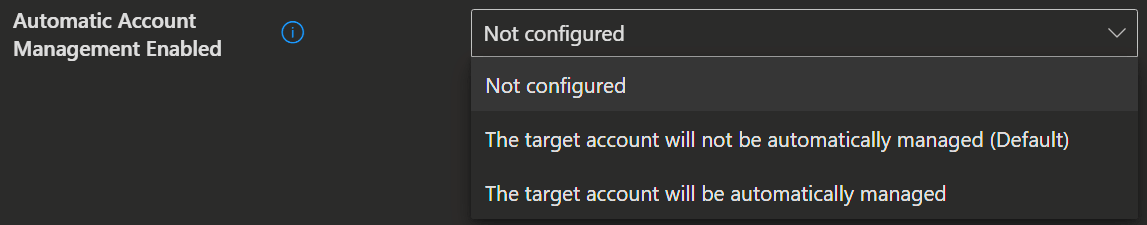
./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementEnabledUse this setting to specify whether automatic account management is enabled.
- If not specified, this setting defaults to False.
| Value | Description |
|---|---|
| false (Default) | The target account won't be automatically managed. |
| true | The target account will be automatically managed. |
Policies/AutomaticAccountManagementNameOrPrefix

./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementNameOrPrefixUse this setting to configure the name or prefix of the managed local administrator account.
- If specified, the value will be used as the name or name prefix of the managed account.
- If not specified, this setting will default to "WLapsAdmin".
Policies/AutomaticAccountManagementRandomizeName
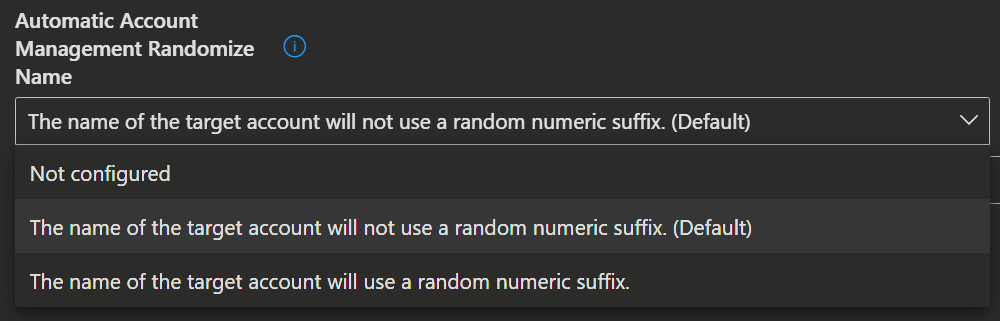
./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementRandomizeNameUse this setting to configure whether the name of the automatically managed account uses a random numeric suffix each time the password is rotated.
- If not specified, this setting defaults to False.
| Value | Description |
|---|---|
| False (Default) | The name of the target account won't use a random numeric suffix. |
| True | The name of the target account will use a random numeric suffix. |
Policies/AutomaticAccountManagementTarget
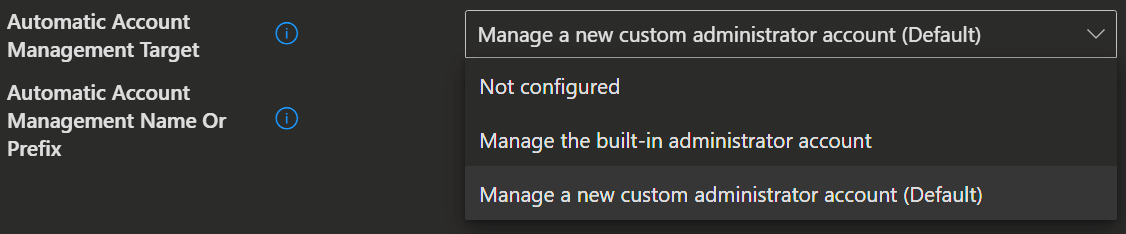
./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementTargetUse this setting to configure which account is automatically managed.
- If not specified, this setting will default to 1.
| Value | Description |
|---|---|
| 0 | Manage the built-in administrator account. |
| 1 (Default) | Manage a new custom administrator account. |
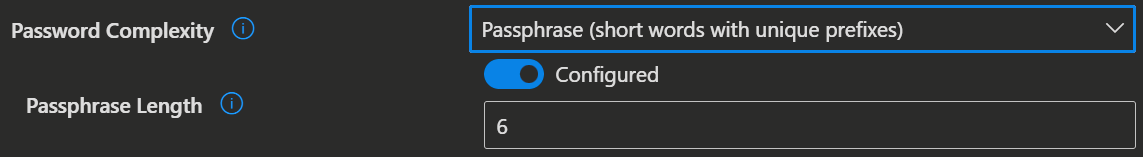
./Device/Vendor/MSFT/LAPS/Policies/PassphraseLengthUse this setting to configure the number of passphrase words.
- If not specified, this setting will default to 6 words.
- This setting has a minimum allowed value of 3 words.
- This setting has a maximum allowed value of 10 words.
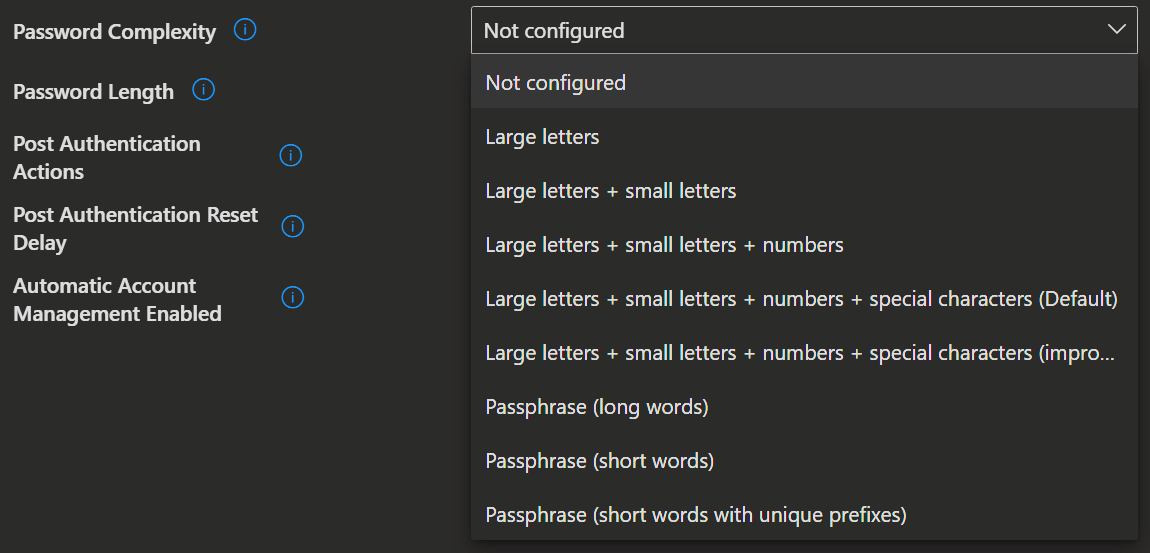
./Device/Vendor/MSFT/LAPS/Policies/PasswordComplexityUse this setting to configure password complexity of the managed local administrator account.
- If not specified, this setting will default to 4.
Passphrase list taken from "Deep Dive: EFF's New Wordlists for Random Passphrases" by Electronic Frontier Foundation, and is used under a CC-BY-3.0 Attribution license.
You can download the 'Windows LAPS Passphrase Word Lists' here.
IMPORTANT
Windows supports the lower password complexity settings (1, 2, and 3) only for backwards compatibility with older versions of LAPS.
| Value | Description |
|---|---|
| 1 | Large letters. |
| 2 | Large letters + small letters. |
| 3 | Large letters + small letters + numbers. |
| 4 (Default) | Large letters + small letters + numbers + special characters. |
| 5 | Large letters + small letters + numbers + special characters (improved readability). |
| 6 | Passphrase (long words). |
| 7 | Passphrase (short words). |
| 8 | Passphrase (short words with unique prefixes). |
Policies/PostAuthenticationActions
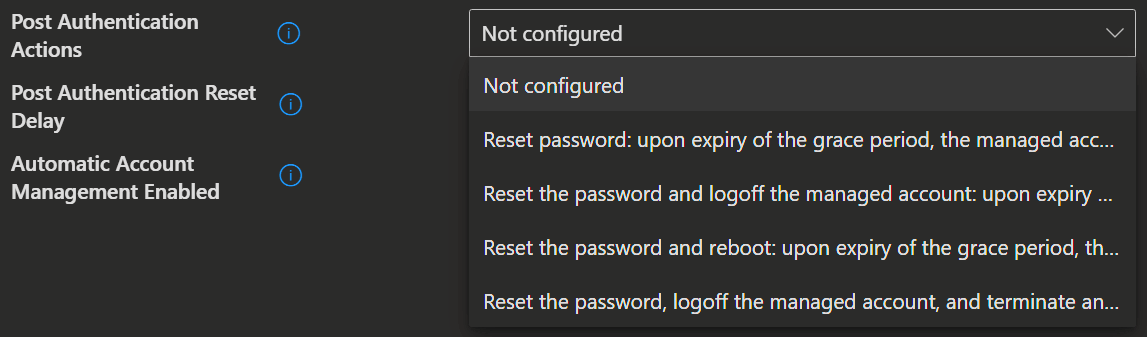
./Device/Vendor/MSFT/LAPS/Policies/PostAuthenticationActionsUse this setting to specify the actions to take upon expiration of the configured grace period.
- If not specified, this setting will default to 3 (Reset the password and logoff the managed account).
IMPORTANT
The allowed post-authentication actions are intended to help limit the amount of time that a LAPS password may be used before being reset. Logging off the managed account - or rebooting the device - are options to help ensure this. Abrupt termination of logon sessions, or rebooting the device, may result in data loss.
IMPORTANT
From a security perspective, a malicious user who acquires administrative privileges on a device using a valid LAPS password does have the ultimate ability to prevent or circumvent these mechanisms.
| Value | Description |
|---|---|
| 1 | Reset password: upon expiry of the grace period, the managed account password will be reset. |
| 3 (Default) | Reset the password and logoff the managed account: upon expiry of the grace period, the managed account password will be reset and any interactive logon sessions using the managed account will be terminated. |
| 5 | Reset the password and reboot: upon expiry of the grace period, the managed account password will be reset and the managed device will be immediately rebooted. |
| 11 | Reset the password, logoff the managed account, and terminate any remaining processes: upon expiration of the grace period, the managed account password is reset, any interactive logon sessions using the managed account are logged off, and any remaining processes are terminated. |
Outcome
If you set up the new settings correctly, the passwords on your devices might look like this:
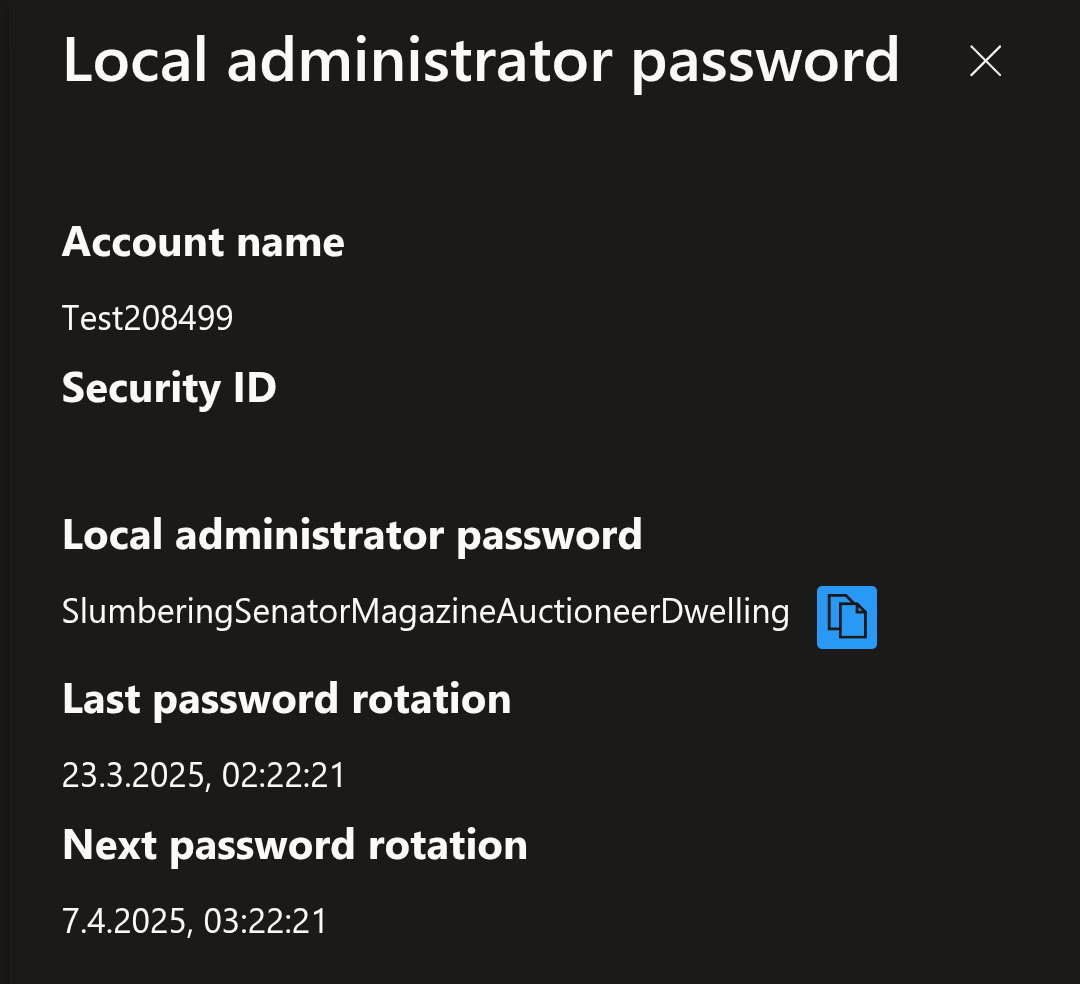
Complete with the new Passphrase and Account randomization.
Of course you can still, trigger a manual password rotation via the Device blade.